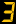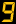Protection For Your Emails & Files
Ensuring Your E-mail Messages & Files Are Not Read
What We Offer
?250GBP will protect your emails
To get the system in full confidentiality?
Phone: 07848 380275 if in the UK
If outside the UK: , or
Click To Contact Secure Email Systems
Foil The Email Hackers
Making sure your messages and files are received without being intercepted
Get total protection from industrial espionage and all types of message hackers
Your messages and files seen by who you?want to read them, not those?who should not
What We Offer
A very simple and 100% secure method of transferring your messages and files without?being read by unwanted third parties?
Introduction
If getting a message or file securely delivered without being read is needed, we have the solution.
Email security is a major problem for businesses and individuals alike. Snooping hackers have turned prying into internet messages an art form in itself.
A totally foolproof way to ensure that the recipient(s) get the message or file without the threat of having a third party intercept it.
There is nothing to download and there is no monthly "licence" fee to pay.
[Full Details]
?
You Think Your Email Is Safe?
British Government Department's Own View On E-mail Security?
Most people are unaware of what happens when they click the 'send' button. It may surprise you to know that it doesn't just go from you to the person you intended to send it to. Although email appears quick, each message hops around the public internet going from system to system...If someone wants to intercept, copy or even alter your emails - and the information they hold - they can do it with relative ease.
[More]Skype & Blackberry: The Faults In Their Security Systems Revealed
?
If you think you are safe sending messages using "secure" methods, read on.
Several organizations state that their systems are safe. Two of these are Blackberry and Skype. Both in their own way portray themselves as secure.
What you may think is totally secure falls down when examined in detail. There is plenty of evidence?detailed showing how insecure they really are.
[More]Problems With Email "Security"
The protection of electronic mail from unauthorized access and inspection is known as electronic privacy. In countries with a constitutional guarantee of the secrecy of correspondence, e-mail is equated with letters and thus legally protected from all forms of eavesdropping. That is the official line for public consumption.
The countries which do not have constitutional guarantees of privacy are even worse.
[More]If you don't know exactly what a hacker is, join the club. Many people don't understand the term or its true implications.
The meaning has changed a bit over the years and through the evolution of the Internet.
In the most familiar sense, a hacker is anyone who attempts to break into computer systems by surreptitious means.
Hire hackers to catch other hackers??
In recent times, "Anonymous" hackers have been wreaking havoc with corporate and government systems. So, should corporations hire these guys?
Leading tech companies have long used "ethical hackers" to help probe vulnerabilities in their systems and software. Should some of the not-so-ethical hackers be added to payrolls as well?
One journalist, Misha Glenny, says there is a solid case to be made for hiring hackers. Delivering his remarks at a recent TED event, Glenny pointed out that groups such as Anonymous tend to be idealistic, and "are providing a service by demonstrating how useless companies are at protecting our data."
How to become a hacker?
You've read about the exploits of groups such as LulzSec, Anonymous and AntiSec.
And, now you want to become a hacker. But, how does one become a hacker?
Is there some secret society with blood rites that tests your willingness to exploit and deliver malicious payloads to unsuspecting computer users?
Or, do you have to sell your soul and pledge allegiance to an organized crime boss to break into this mysterious field?
How Much Is It?
?250GBP for Primary 1
The Enigma machine (above) was thought by the Germans to be foolproof; it wasn't. Their messages were read by the British. Make sure nobody reads your messages.
SECURITY ALERTS
From Sophos, ZD Net & Other Internet Expert Groups
London's Met Police uses 'blanket tracking system' to intercept, remotely shut down mobile phones?
London's Metropolitan Police, headquartered at Scotland Yard, has been accused by privacy campaigners of violating citizens' privacy and civil liberties, after it was discovered that the police service had acquired military-grade surveillance equipment to track and if necessary, disable mobile phones.
London's police service has been under increased pressure to bolster its provisions post the London riots during the summer, in the run up to the Olympic games next year. Yet, privacy campaigners are concerned with the police service becoming ?another MI5?.
A Freedom of Information Act request to Scotland Yard shows that the police service paid ?143,455 ($230,000) to Datong plc. for "ICT hardware" in 2008/2009, with Hertfordshire police service paying ?8,373 ($13,300) in February 2011.
READ FULL STORY?
Nubile female film stars will be breathing a sigh of relief today at the news that the FBI has arrested a man suspected of hacking into celebrity's phones and emails accounts and stealing their invariably nude photos.
Hackers successfully broke into 93,000 accounts at Sony over the last few days, once again impacting users of the Sony Entertainment Network, PlayStation Network (PSN) and Sony Online Entertainment services.
The Feds have obtained access to WikiLeaks volunteer Jacob Appelbaum's email accounts with the help of a law that lets them go after email and cellphones without a search warrant.
Microsoft's Patch Tuesday bulletin for October 2011 covers 23 vulnerabilities in 8 patches. Affected software includes all supported versions of Windows, Internet Explorer, .NET, Silverlight and more.
Phishing emails pretending to be from UPS.com are making the rounds in an attempt to steal your credentials for the My UPS website. Find out what to look for and stay safe online.
RSA has revealed that it believes two groups, working on behalf of a single nation state, hacked into its servers and stole information related to the company's SecurID two-factor authentication products. But for some reason it's declining to say which country..
Jeremy Kyle, the UK's answer to Jerry Springer, is the subject of a fast-spreading Facebook scam that claims he was "attacked by a chav". Don't be a dumbo, don't click on the links as you'll only be sharing the scams with your Facebook friends.
'Government' backdoor R2D2 Trojan discovered by Chaos Computer Club
A Trojan horse allegedly created by the German government to spy on citizens' online activity and Skype conversations has been discovered. Sit back, grab your popcorn, and get ready for the political storm if this proves to be true.
Read More
Malware strikes USAF Predator drone computer systems
Malware has infected the control systems used by the United States Air Force to fly Predator and Reaper drones, logging keypresses as the unmanned aircraft are flown remotely in Afghanistan, Libya, Pakistan and other conflict zones.
Read More
Steve Jobs's death exploited by scammers
It's impossible to express how sad many people in the technology world feel at the news of the death of Steve Jobs.? Sickeningly, scammers were waiting to take advantage of the bad news.
Read More
How the m00p malware-writing ring was busted
The Virus Bulletin conference is told about the investigation into a modern malware-writing gang. But with only two of the cybercriminals sentenced, was justice really done?
Read More
U.S. issues secret, warrantless court order for email data of Wikileaks' volunteer?
The U.S. government used a controversial electronic eavesdropping law to force Google and a small Internet service provider into handing over email account data of a Wikileaks volunteer, the Wall Street Journal reported overnight.
Using a controversial law, the Electronic Communications Privacy Act ? which allows the government and law enforcement to obtain email and phone records without a search warrant ? one of the companies fought the order through legal channels, but lost.
Full Details
German government accused of spying on citizens with state-sponsored Trojan?
A well-established group of German hackers, the Chaos Computer Club, has accused the German government of releasing a backdoor Trojan into the wild. According to Mikko Hypponen of F-Secure, the announcement was made public on the group's website in the form of a 20-page PDF (in German).
The accompanying English-language post claims the group reverse-engineered and analyzed the program, which it calls "a ?lawful interception' malware program used by German police forces".
F-Secure sidestepped the thorny question of where the Trojan came from, saying, "We do not know who created this backdoor and what it was used for. ... We have no reason to suspect CCC's findings, but we can't confirm that this trojan was written by the German government. As far as we see, the only party that could confirm that would be the German government itself."
The company further added, "We have never before analysed a sample that has been suspected to be governmental backdoor. We have also never been asked by any government to avoid detecting their backdoors."
Full Details
Hacking Group Expose Possible German Gov't Trojan Program

German police are alleged to have released a malware program to spy on people through their computers?
The largest European hacker club, "Chaos Computer Club" (CCC), has reverse engineered and analyzed a "lawful interception" malware program used by German police forces.
It has been found in the wild and submitted to the CCC anonymously.
The malware can can not only siphon away intimate data but also offers a remote control or backdoor functionality for uploading and executing arbitrary other programs.
Significant design and implementation flaws make all of the functionality available to anyone on the internet.
Re-published with kind permission of the Chaos Computer Club
[More]
China's Green Dam and the cyberwar implications
Chinese military leaders have always been aware of the military advantage the US has over the People's Liberation Army. Reading through their published assessments of Sino-US war possibilities confirm our belief that we would dominate them in the air, land and sea. However the PLA was born of asymmetric warfare and this remains a core part of their strategies against any possible wars with the US. Specifically the PLA writes about the use of cyberwarfare as a means of countering this imbalance.
Full Details
Major security hole claimed in some HTC Android smartphones
Security researchers claim they've found an insecure logging program in some HTC Android phones that easily enables crackers to get full access to all your personal data.
Full Details
Kaspersky: 12 different vulnerabilities detected on every PC
Researchers from Kaspersky have sampled their customer base, and found out that on average, every PC has 12 different vulnerabilities.
Full Details
RIM warns of BlackBerry code execution security flaws
Vulnerabilities exist in how the BlackBerry MDS Connection Service and the BlackBerry Messaging Agent process PNG and TIFF images for rendering on the BlackBerry smartphone.
Full Details
RIM warns of data leakage, denial-of-service vulnerability
Research in Motion (RIM) has shipped a patch to cover a serious security vulnerability that could allow attackers to read files that contain only printable characters on the BlackBerry Enterprise
Full Details
Tackling the risk of cyber-security attacks
The growing number of cyber attacks has become one of the most serious economic and national security threats our nation faces.
Full Details
China hardest hit by latest IE zero-day attacks
The attacks, first spotted on March 9, included Trojan downloaders and backdoor programs that gave malicious hackers full access to hijacked PCs.
Full Details
How to Find Vulnerabilities Before Attackers Do
Today's cybercriminals are smart. They know that the fastest way to attack the network is with web-based malware that exploits known vulnerabilities in the software and operating systems.
Full Details
Kaspersky denies leaks after SQL hack
The U.S. website of the Russian antivirus vendor was hacked and the company's customer database exposed, but Kaspersky denies data was compromised.
Full Details
Cisco patches Security Manager flaw
The company has released an out-of-cycle patch for a vulnerability that could enable a successful attack on Cisco security products.
Full Details
Skype: Video chat feature meets code execution vulnerability
Updated below: Aviv Raff, a security researcher, has found a flaw in Skype that could allow an attacker to control your PC.
Full Details
Smart security: network scanners
Before a hacker reveals the gaps in your network security, do it yourself. Using a network vulnerability scanner is like hiring a hacker, only the intelligence is artificial.
Full Details
Security: Stop ignoring the obvious mistakes
The FBI is taking one of the key goals of the just released draft of the National Strategy to Secure Cyberspace to heart.
The law enforcement agency, best known for its Most Wanted list and inept use of information technology, is hoping to build awareness about cybersecurity and promote good security hygiene.
In his recent ZDNet News commentary on keeping hackers at bay, Arvind Krishna, vice president of security products for Tivoli Software at IBM, quoted from the FBI's list of five common mistakes that leave company and employee data vulnerable
Full Details
?
?250GBP will protect your emails
To get the system in full confidentiality?
Phone: 07848 380275 if in the UK
If outside the UK: , or
Click To Contact Secure Email Systems